Update 2010-04-07: Source code now available: http://github.com/eoftedal/MalaRIA-Proxy
Introduction
Unrestricted crossdomain.xml and clientaccesspolicy.xml files can be abused by an attacker. The attacker can setup a rouge RIA app - a malaRIA - on a site, and if he can trick the user to visit the site, the malicious RIA can perform actions on behalf of the user (CSRF). Because the RIA runs in the user's browser, the requests will reuse the user's authentication cookies. Because the RIA is able to both read and request data, normal CSRF protection does not work (nonces/tokens can be read).
Such a RIA can at the same time transfer data back and forth to the server from which it came through a socket. This can allow the attacker to send commands to the RIA, which will then perform these actions.
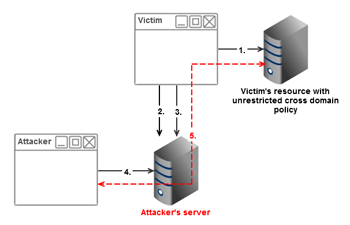
The MalaRIA proxy
The MalaRIA proxy consists of a silverlight or flex RIA application running in the browser and a java backend. The attack works like this:
- The victim logs in on site A
- The victim accesses evil site B and loads the RIA app
- The RIA app connects back to the java backend
- The attacker sets his browser to use the java app as a proxy in his browser
- A request to the proxy, is sent to the RIA app, which on behalf of the victim, gets the resource, and passes it back to the attacker
Here is a video showing the components in action:
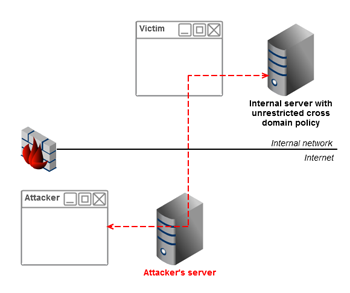
Attacking the intranet
Because the attack goes through the user's browser, the attacker may be able to gain access to an intranet server if that server has an unrestricted crossdomain.xml or clientaccesspolicy.xml. To detect an internal server the attacker can use referer headers, javascript port scanners, CSS history hacks etc. Jeremiah Grossman talked about attacking the intranet using javascript malware at Blackhat'06.
Update 2010-04-12: Adam tipped me about the post "Penetrating Intranets through Adobe Flex Applications" on how to exploit insecure proxy-config.xml through BlazeDS to attack the intranet. The authors have built a tool called Blazentoo to exploit such configs.
Limitations
The current PoC does not support images and documents due to encoding issues. It should be possible to fix this, and thus this could potentially be used to also steal documentation.
Update 2010-04-14: Images and documents now supported.
Protection
Restrict access in your crossdomain.xml and clientaccesspolicy.xml files.More information
- Why you need to lock down your crossdomain.xml
- Why you need to lock down your Silverlight clientaccesspolicy.xml
- The Dangers of Cross-Domain Ajax with Flash
Re:
It happens automatically. All requests made from the browser to a given server, will include the cookies for that server (unless the secure flag is set for the cookie and the connection is not https anymore). A request from the RIA is treated like any other request (request for a script from a script tag, image from an image tag etc.) and thus includes the cookie.This, among other reasons, is why smart people use things like NoScript and FlashBlock to supplement their own judgement... though they'd still be useless with an attacker smart enough to trick them into allowing the malicious RIA.
http://www.andlabs.org
Awesome work!The approach is so fresh. I am currently developing something similar but you beat me to it :)
Since the source code is out am going to read through and see if I can steal a few ideas, hope you dont mind ;)
Moonlight?
Hello, does this vulnerability also affect the Moonlight plugin from the folks at Mono-devel?Re: Moonlight?
I haven't tested it with the Moonlight plugin, but I think it does, because this is not a flaw in silverlight (or flex). The problem is the unrestricted policy set on the website.I will share my pre-release version with you very shortly, still coding. Think our tools might complement each other. thanks!
http://www.gdssecurity.com/l/b/2010/03/17/penetrating-intranets-through-adobe-flex-applications/
...?
I do this. I create my site and victim browser go to www.attacker.com/malariaflexproxy.html But all what I see in victim browser is:
_________________________________
Connecting back to malaria server...
Connected and ready
Got data from proxy
Trying: [GET http://www.gmail.com/ text/html, ]
Sent
_________________________________
And nothing else. No data was received. What's wrong?
You are doing it right, however MalaRIA proxy was built to highlight the problem with open crossdomain.xml and clientaccesspolicy.xml files, meaning it only works if the target site (not the site hosting the flash/silverlight app) has an unrestricted such policy:
http://erlend.oftedal.no/blog/?blogid=101
http://erlend.oftedal.no/blog/?blogid=102
In your case, www.gmail.com does NOT have such a policy (which is good, or else anyone could read your email by deploying MalaRIA or another flash/flex/silverlight application on their site). The same origin policy is meant to block this kind of traffic, however the flash/flex/silverlight relaxes this policy using the crossdomain.xml/clientaccesspolicy.xml files.
Does it mean, theoretically I can get access to victim browser if he going by link on my malware-site? But MalaRIA doesn't allow this.
If a victim accesses malware server A, code from A can only access other data from A, unless
a) a site B has an open cross domain policy (in which case MalaRIA) can be used,
b) site B has an XSS flaw, which can be used to inject something like BeEF
c) malware server A contains an exploit which turns the user's computer into a zombie.
